Proactive risk management (PRM) is essential for companies looking to remain compliant, secure and operational, avoiding a host of internal and external challenges by getting in front of them. For organisations, PRM is a forward-looking and prevention-focused approach to identifying the root causes of risks. Rather than firefighting when things go wrong, PRM allows you to preempt and avoid potential risks by adjusting your processes and procedures.
For instance, PRM could have prevented three EU asset management and brokerage companies paying a combined €37 million in fines for breaching the Market Abuse Regulation (MAR) when employees from each carried out ‘wash trades.’ These involve the same party, or multiple parties working together, buying and selling the same financial instrument to give a false impression of demand in the market. It is estimated that the companies’ clients lost out on nearly €50 million as a result of these actions. Had there been adequate conflict of interest or employee personal trading procedures in place, it could have been proactively avoided.
With rising geopolitical uncertainty around the world, stricter regulations and growing digital complexity due to artificial intelligence entering all aspects of life, PRM is a necessity for all businesses. This article provides proactive risk management examples to help you shift your corporate mindset to engaging this preventative approach.
|
Table of Contents
|
Key takeaways
- Proactive risk management shifts companies from firefighting unexpected events to a forward-looking approach to prevention by identifying root causes and adjusting processes before breaches occur.
- Combining qualitative insights, quantitative data and processes like FMEA helps prioritise critical risks such as spoofing, insider misuse and weak whistleblowing culture.
- Clear treatment plans with owners, deadlines and dedicated technology turn risk findings into concrete actions rather than theoretical concerns.
- Ongoing monitoring of key risk indicators (KRIs), incidents and surveillance alerts is essential to refine controls as new patterns and threats emerge.
- A proactive approach strengthens the first line of defence, improves transparency for leadership and investors and turns robust compliance into a strategic and competitive advantage.
Proactive vs reactive risk management
|
Element |
Proactive risk management |
Reactive risk management |
|
Timing |
Preventive: works before an incident happens by scanning for vulnerabilities, weak controls and emerging risk trends. |
After the fact: activated only once an incident or breach has already occurred. |
|
Focus |
Targets root causes, such as poor access control, weak training or unclear ownership, to stop issues recurring or ever arising. |
Focuses on isolated events, fixing the immediate problem without always resolving underlying drivers. |
|
Analysis |
Uses predictive methods like key risk indicators (KRIs), trend analysis, horizon scanning, stress tests and scenario analysis to anticipate where things may go wrong. |
Uses retrospective review in the form of incident reports, post-mortems and forensic analysis, for example, to understand what went wrong and who was affected. |
|
Compliance orientation |
Aligned with modern frameworks that expect ongoing prevention and resilience, such as ISO 27001, NIST RMF and ISO 37301. |
Often limited to meeting minimum incident response or reporting duties. May satisfy formal notification rules but can fall short of regulatory expectations on robust systems and controls. |
|
Typical activities |
Risk assessments, control design, automation, training, playbooks, simulations, vendor due diligence, culture and whistleblowing programmes. |
Breach notification, damage control, manual remediation, disciplinary measures, ad hoc control fixes, regulatory responses. |
|
Impact on risk profile |
Reduces likelihood and impact over time. Builds resilience, trust and audit-ready evidence of due diligence. |
Contains damage once exposed but can leave the organisation vulnerable to repeat issues and higher regulatory scrutiny without implementing proactive measures too. |
How to implement proactive risk management step by step
1. Carry out regulatory horizon scanning
Risk management does not stand still and there are always new pieces of legislation and updates to current laws being developed and implemented. Regulatory horizon scanning is a proactive method of anticipating changes, based on consultations and proposals so that you can work to develop effective controls before you are within the scope of an active regulation.
Understanding when you will need to develop controls and the nature of these protections to both meet regulatory requirements and protect the company from emerging threats helps you integrate solutions early and ensure they are working effectively when needed.
Example: Early knowledge of the EU Listing Act could have helped companies prepare for the clarification that only the final event of protracted process qualifies as inside information. This would have given them time to understand the definition of a ‘final event’ to ensure compliance after the implementation and to adjust internal workflows to meet the new, less burdensome framework immediately, making the most of efficiency savings as soon as the new rule came into effect.
2. Identify risks and context
Each company’s risk exposure is different, so you need to map those operational, compliance, financial and reputational threats that are specific to your organisation, sector and country.
Look at past incidents to understand what potential risks might occur, consult internal stakeholders across departments, look at regulatory changes on the horizon and carry out a SWOT analysis to uncover strengths, weaknesses, opportunities and threats. Consider issues that your peers have faced in recent years and consider whether they could also be pertinent to your business.
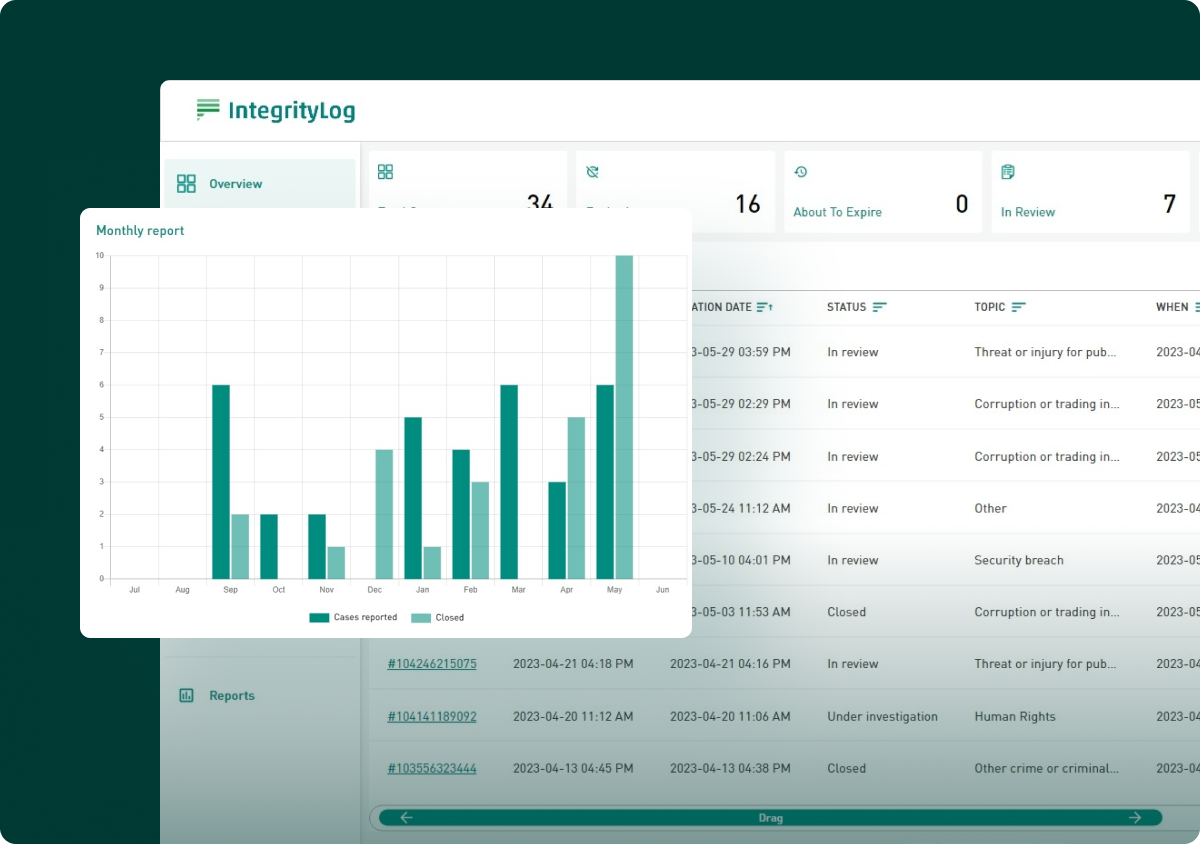
Example: If you have a weak speak-up culture and poor retaliation prevention processes, there could be a high risk that employees do not surface serious concerns. This could result in a regulatory breach and reputational damage. Allowing confidential and anonymous reporting through a platform like IntegrityLog encourages reluctant whistleblowers to share their evidence of wrongdoing without their identity being revealed.
3. Assess prospectively
Once you understand those potential threats that apply to your business, you can consider how they might play out and what the implications they would have if they came to fruition. Think about the possible outcomes and the likelihood of them occurring, prioritising those that are most pressing and which would be most impactful.
A failure mode and effects analysis (FMEA) helps you take a systematic approach to help you make this assessment and understand what might occur in the short, medium and long term. You take each function, identify its failure potential, the consequences, the severity of the repercussions and then look into the root causes to identify ways to prevent these critical risks from occurring.
Example: From your analysis, you might rate spoofing as a high-priority market abuse risk that could cause a conflict of interest with your clients. The FMEA shows you that, because it can occur at high frequency and distort order books in real time, it would have a greater impact on client and investor confidence than other forms of market abuse. It may also be that you currently have no dedicated surveillance plan in place to spot such activity.
4. Plan treatments
Using the results of your analysis, you will be left with a list of risks, ranked in order of priority. This helps you decide where to allocate resources for the most effective proactive risk prevention. Go through the list with your team and decide which risks you will accept as part of your company’s risk appetite, which you need to mitigate and which you can transfer.
For those that require action, target your approach to each with specific mitigation strategies. Designate each to a team member or department and set a deadline for completion. This adds accountability to the measures you put in place and makes it more likely that they will be seen through.
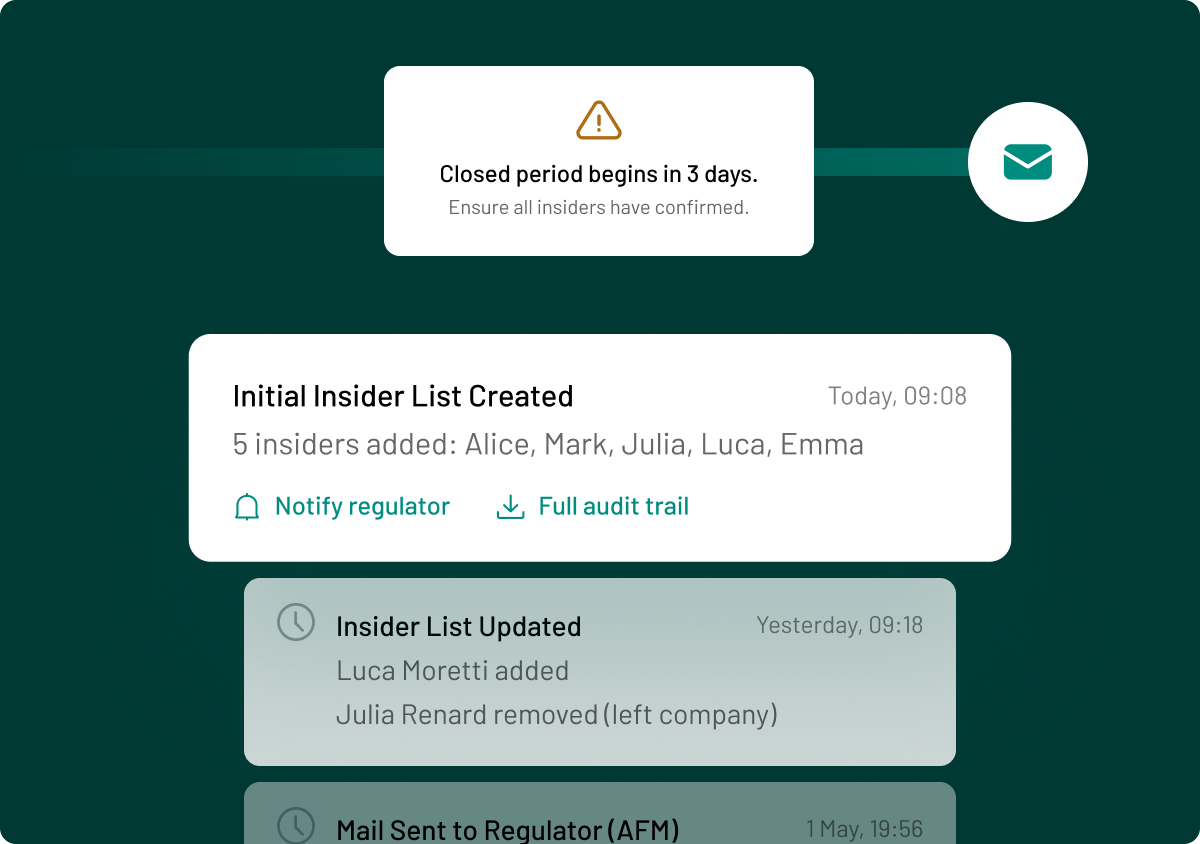
Example: If you currently use a spreadsheet for insider list creation and management, there is a risk of losing track of version control, submitting lists in the wrong format and failing to archive all previous versions of each insider list. This could lead to a sanction of 0.8% of annual turnover or €1 million. A proactive mitigation would be to implement a digital insider list solution like InsiderLog, which ensures your lists are in the correct, ESMA-approved format and that each iteration is saved for your audit trail.
5. Monitor and refine
For the controls you put in place for proactive risk management, track their performance to ensure they are doing their job correctly and helping you avoid risks. Incident records, KRIs and regular testing of your controls will help you see what is working and which approaches you need to adjust.
Policy management is key to understanding exactly which procedures you have in place and who owns them and is responsible for reporting on them. Use this knowledge to take a deep dive into the performance of these controls and truly understand where they can be improved to increase efficiency and effectiveness.
When you identify new patterns and risks, carry out another FMEA and, if necessary, add new controls and update your policies. Revisit your training programme to include the new information and keep your risk assessment up to date, reflecting the new status of your PRM approach.
Example: If your trade surveillance tool starts flagging more late disclosures or unusual staff trades around results days, you should review the alerts, tighten your approval process and remind teams about closed-period rules.
Manage regulatory demands with confidence
As the regulatory demands on company’s become more complex, a proactive risk management approach becomes vital to understanding where gaps are. Euronext Corporate Solutions’ package of secure regulatory compliance solutions will help you fill those gaps and digitise manual processes for a more robust approach to compliance.
Request a demo today |
Benefits of proactive risk management
- Strengthens your first line of defence by spotting potential flaws before they are exploited. You equip your teams with practical controls and targeted training so they can manage threats in their daily working routine.
- Understand your risk environment because it compels you to map your products, processes, markets and regulatory obligations so you gain an in-depth understanding of which risks really matter, rather than treating all potential issues as equals.
- Turn risk into a strategic and competitive advantage by using the actionable insights from your risk assessment to make better decisions going forwards. You can also be more confident of avoiding major detrimental activity and win the trust of investors who are looking for less risky issuers to work with.
- Gain necessary visibility into the right priorities by building dashboards and reporting that highlight where your most pressing risks are. This allows leadership teams to allocate the resources to where they are most needed without guesswork.
Overcoming implementation challenges
Although the benefits for PRM are compelling, some obstacles may remain as you transition to this new way of managing risk. Here are some of those challenges and methods to overcome them.
|
Challenge |
How to overcome |
|
Culture |
You need to harness the tone from the top and have leadership show commitment to the change in risk culture. It can be a significant focus shift to move to PRM, so a united display of support for the new approach is necessary to sell it at all levels of the business. |
|
Data silos |
Different departments may hold information specific to risks that affect them independently, which prevents adequate oversight on risk mitigation. Centralise all risk information and standardise KRIs and other methods of ranking and prioritising risks. |
|
Collaboration |
Regular training is essential for collaboration across departments. You also need to improve internal communication to allow functions to talk clearly to each other and share progress. |
FAQ
1. How does risk assessment contribute to proactive risk management?
Risk assessment identifies and prioritises potential issues before they materialise, allowing you to design targeted controls, allocate resources efficiently and reduce the chance and impact of regulatory breaches.2. What is the difference between predictive risk management and proactive risk management?
Predictive risk management uses data and analytics to forecast where risks may emerge, while a proactive risk management approach is broader, involving acting early, using those insights plus governance, controls and culture to prevent or minimise those risks.
3. How do organisations manage risks that are currently unknown or unforeseen?
They build resilience through strong governance, diversified controls, incident response plans, robust change management and a healthy speak-up culture so new risks are detected, understood and addressed quickly.
4. Can unknown risks be managed proactively?
Yes, by designing flexible systems, monitoring leading indicators, running scenarios, empowering employees to report concerns and regularly reviewing controls, you can limit the damage from risks you could not fully predict.
Conclusion
These proactive risk management examples show how you can implement this way of working into your organisation. Taking a proactive approach helps you understand, assess and prioritise the risks most relevant to your business and mitigate them effectively before they cause a problem and lead to unexpected losses and create financial, regulatory and reputational damage.
Euronext Corporate Solutions’ comprehensive regulatory compliance solution provides digital platforms that improve your risk protection whilst reducing manual work and minimising errors. The platforms in the package help you prevent compliance risks and support you in improving MAR adherence, employee trading oversight, whistleblowing report management and meeting your global LEI obligations. To see how this package works for your business in meeting its compliance requirements, request a demo today.
Request a demo today to find out how to reduce compliance risk |
References and further reading
Related Articles
See all postsThe 8 Most Effective Compliance Risk Assessment Methodologies
07-01-26
Measure Conduct Risk: 7 Key Risk Indicators To Track
31-01-24
How To Create A Compliance Risk Assessment Questionnaire
31-01-24
Why And How To Develop A Compliance Risk Management Framework
26-04-23
How To Fill In Your Compliance Risk Assessment Matrix + Template
14-03-23


.png)
.png)









.png)
.png)













.webp)





