With such a large volume of transactions flowing through the European markets, trade surveillance is essential. For the sake of fairness, stakeholder value and maintaining compliance in the face of an ever more stringent regulatory landscape, issuers must do everything they can to seek out, capture and report unethical behaviour. But there are a number of trade monitoring challenges to overcome.
Unfortunately, there will always be those who attempt to bend the rules, as in the case of Irish businessman Philip Lynch. Lynch was a director of drinks company C&C when he became aware of the chief executive’s decision to step down. This was non-public, inside information, as was the knowledge that the leader of a rival company was in the running for the job. Lynch then bought 200,000 C&C shares. A court found in May 2022 that he had committed insider trading and fined him €75,000, banning him from financial services for five years.
Increasing monitoring of trades is a key element to preventing market abuse, manipulation and distortion, but compliance departments then have to deal with issues such as an overwhelming number of false positives, difficulties in measuring the success of their programme and more. This article explores the challenges with trade surveillance and solutions to increase the efficiency and effectiveness of your efforts.
1. What is personal trade monitoring?
Trade monitoring (or trade surveillance) is the act of monitoring the transactions carried out in your company to ensure they do not amount to market abuse or stray into illegality.
There are two main European Union regulations covering illegal trading activity and market abuse. They are the Market Abuse Regulation (MAR) and the Markets in Financial Instruments Directive (MiFID II). Here is their scope relating to market abuse and the kinds of activities that your trade surveillance efforts should be alert to.
| Legislation | Area | Requirements |
|---|---|---|
| Market Abuse Regulation (MAR) | Inside information | Preventing the unlawful disclosure of specific, non-public information that would affect the price of a financial instrument if it were to go public. In addition, preventing insiders from using that information to inform their trades. |
| Market manipulation | Preventing parties from giving misleading signals regarding the supply and demand of a financial instrument or its potential price. | |
| Market soundings | Understanding the correct manner to communicate sensitive information before a transaction is announced. | |
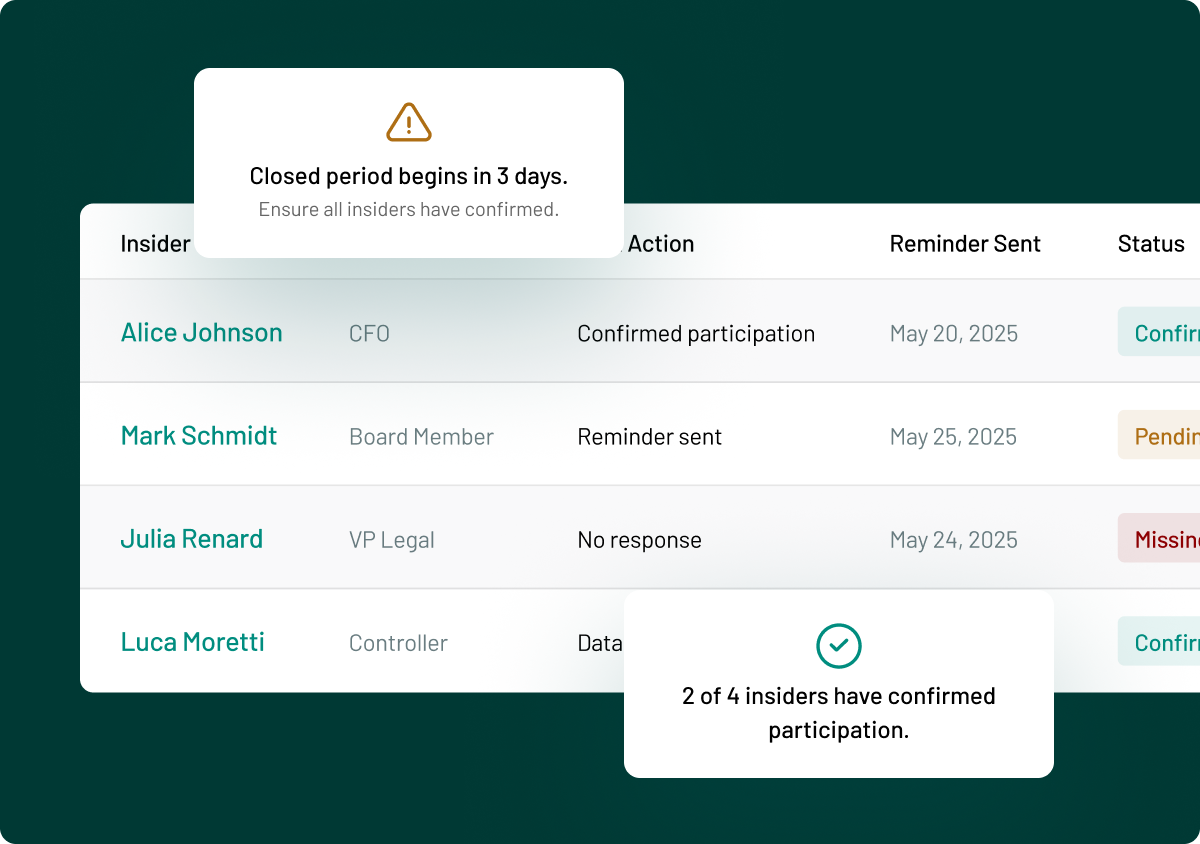
| Persons discharging managerial responsibilities (PDMRs) | Making sure PDMRs notify relevant authorities of any order or transaction undertaken on their personal accounts that relate to the issuer above the reporting threshold and adhere to closed periods. | |
| Markets in Financial Instruments Directive II (MiFID II) | Recording requirements | Ensuring employees capture records of telephone calls, electronic messages and face-to-face meetings that relate to transactions made for a financial instrument, or transactions that were intended to be made. |
| Employees’ trades | Monitoring employees’ trades to prevent conflicts of interest with clients or other illegal activity. | |
| Reconstructing trades | Being able to reconstruct the events that led to a trade in order to prove that you took all steps necessary for compliance. |
2. 5 Employee personal trade monitoring challenges and how to prepare
2.1 Challenge #1: Lack of proactive approach
One issue that compliance departments face is that their trade monitoring systems are reactive. They do flag non-compliant behaviour, but only after it has happened and caused damage.
Yes, the company might take swift action to stop illegal activity and reprimand those responsible for it. However, this is no guarantee that the regulator will look upon the case favourably when investigating it, and there is still likely to be some kind of sanction forthcoming. In addition, the reputational damage from public knowledge of non-compliance could be incredibly detrimental to the business.
Proactive monitoring efforts are desirable, as they prevent such problems from occurring in the first place. For example, making employees seek permission to make trades on their personal accounts can filter out potential market abuse attempts.
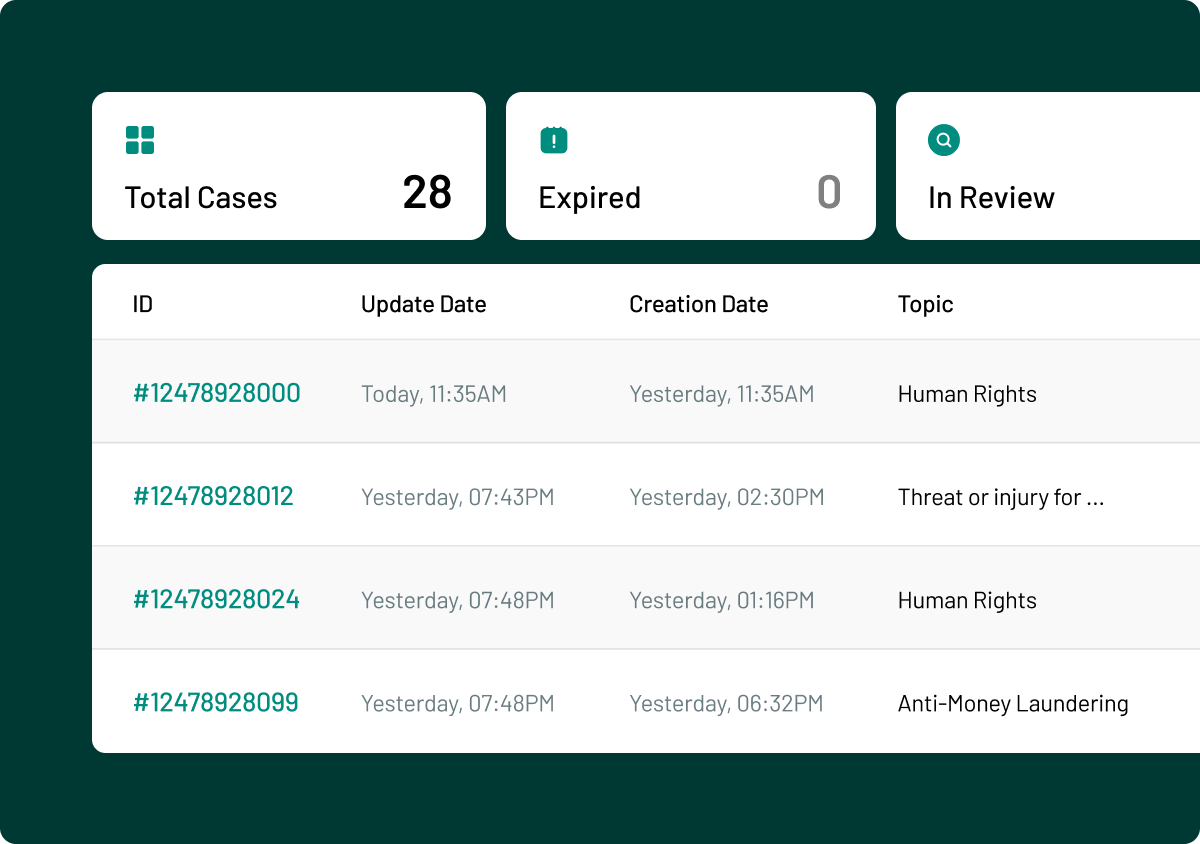
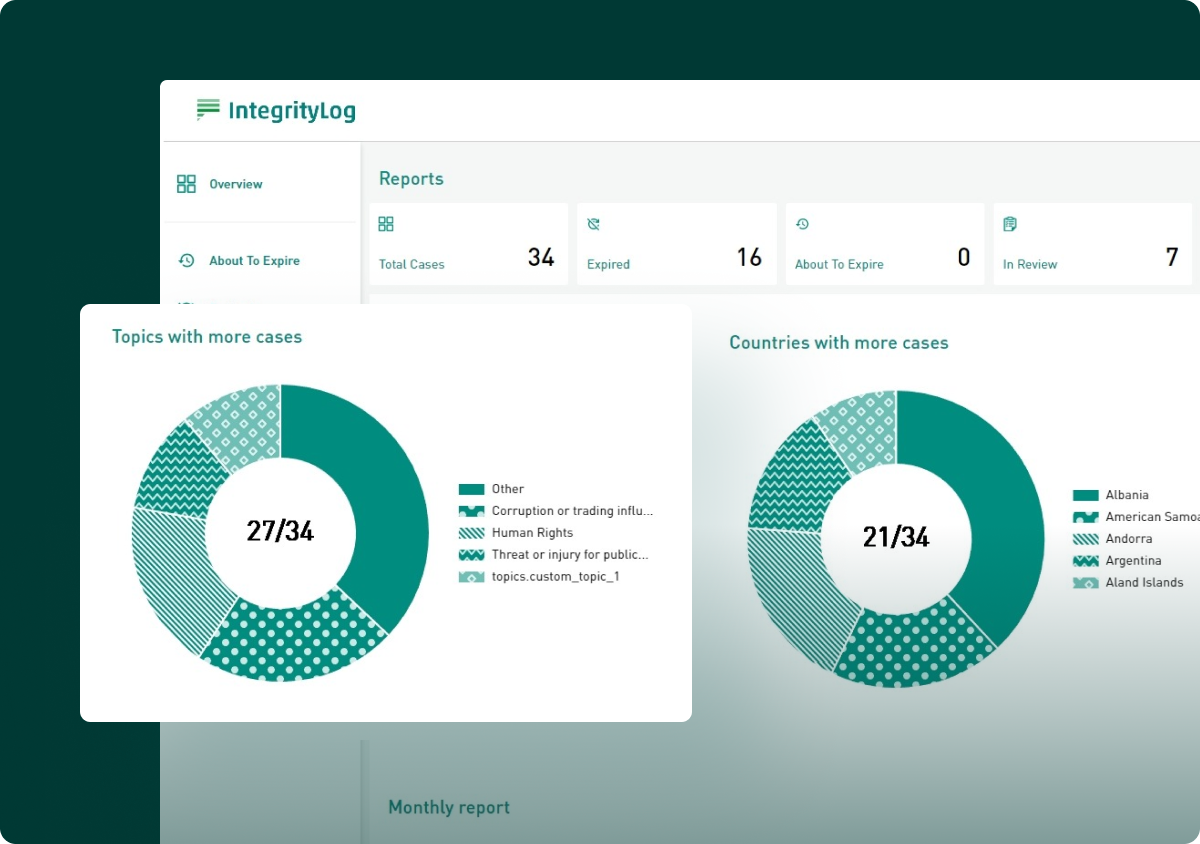
Tools such as those within InsiderLog, allow firms to manage the process of accepting or declining permission for employees to trade in securities that would risk non-compliance. This prevents attempts at market abuse before they take place.
2.2 Challenge #2: Difficulty measuring success
The trouble with an effective trade monitoring programme is that you want it ideally to prevent illegal activity, and that makes it difficult to measure success. It is impossible to understand how many incidents you prevented with your surveillance efforts because no one is going to admit that they would have committed market abuse if they thought they could get away with it.
Carrying out an in-depth risk assessment for your company is one way to show the relevance of your monitoring programme. This includes creating a data-driven assessment of the market abuse risks for each area of your business and keeping it updated as the business grows and changes. Understanding where the risks are and what the likelihood of non-compliant behaviour is in these areas helps you tailor your surveillance efforts accordingly and prove their necessity to senior leadership.
2.3 Challenge #3: High volume of false positives
With so much data flying around, your trade surveillance system could accidentally flag activity as being non-compliant when it is actually not. This is termed a false positive, and there are a number of reasons why it can happen.
For example, one trader could buy a security at the same time as another unconnected colleague looks to sell the same security. If this was the same trader, it could look like market manipulation aimed at creating a false impression of the activity around that security.
Avoiding this requires greater data analysis and machine learning to understand which behaviours are of concern and which just give that impression without context.
2.4 Challenge #4: Investigation is costly and time-consuming
Compliance departments do not have unlimited resources, and investigating surveillance alerts can drain both money and time for the team.
One solution to reduce the amount of investigation time needed is to concentrate on prevention. This means focusing your efforts on deterrents, such as sanctions for non-compliance, while also creating an effective compliance culture.
Promoting functions such as your whistleblowing procedure creates an environment where everything is run through the prism of compliance.
2.5 Challenge #5: Difficulty monitoring the use of personal devices
MiFID II requires all conversations, written and verbal, to be recorded when they concern trades. Within the office, where company landlines are used, this is straightforward. However, all employees have their own devices and may sometimes choose to use them for work purposes. This creates a situation in which you lose control over whether the calls are recorded.
The European Securities and Markets Authority (ESMA) stated that “a firm shall take all reasonable steps to prevent a relevant person from making, sending or receiving relevant telephone conversations and electronic communications on devices which the firm is unable to record or copy.”
You need a stringent Bring Your Own Device (BYOD) policy in order to ensure that you avoid market abuse. You must instil in employees the importance of the recording requirements within MiFID II.
3. How personal account dealing compliance software helps
Personal account dealing monitoring software digitises the process of pre-clearing and monitoring employees’ personal trading activity.
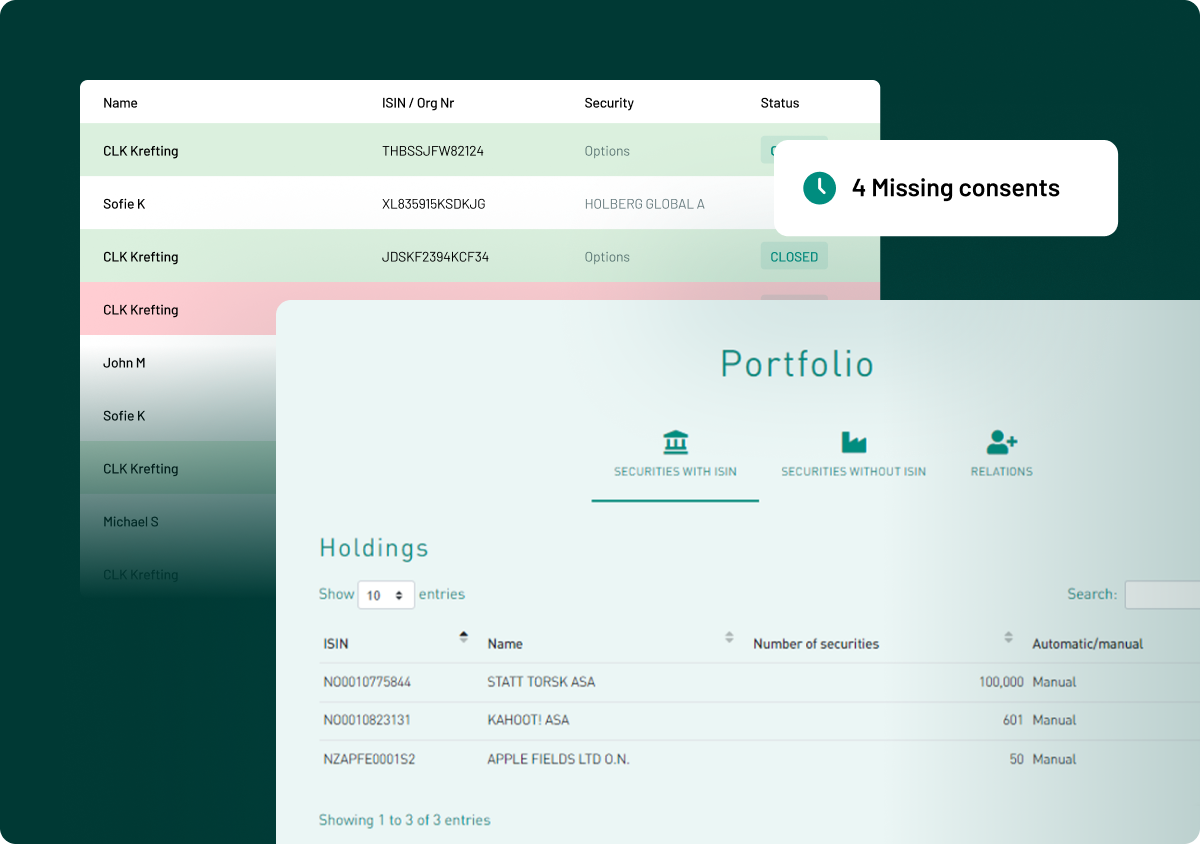
With InsiderLog’s pre-clearance features, you can get a complete overview of insider trades, linking each transaction to a specific person. From pre-approval and reporting of PDMRs’ trades to monitoring closed periods and setting custom thresholds, the platform helps you centralise your workflow and stay compliant effortlessly.
4. FAQs
4.1 What are the types of market abuse?
The types of market abuse are:
- Insider dealing
- Unlawful disclosure
- Misuse of information
- Manipulating transactions
- Manipulating devices
- Disseminating misleading information
- Distortion and misleading behaviour
4.2 How do you track insider trading?
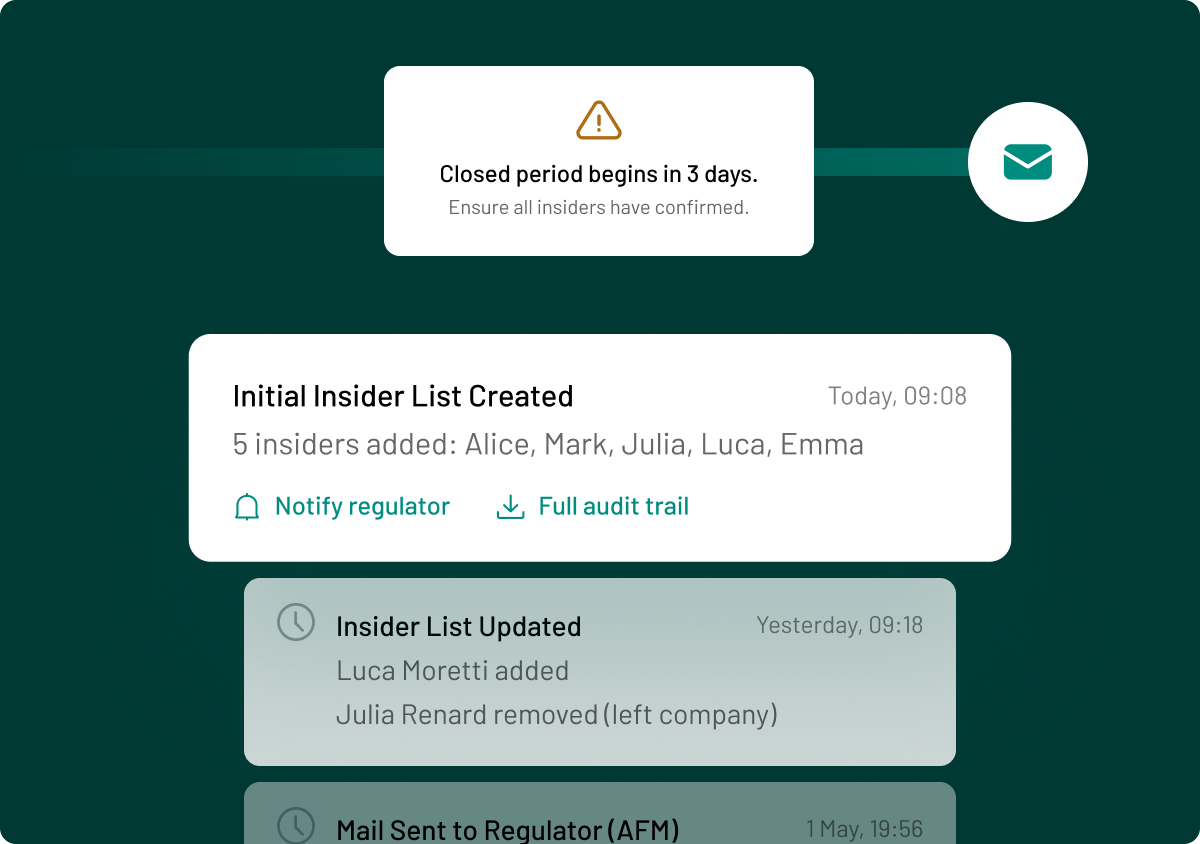
When employees gain access to inside information, you must place them on an insider list. This shows who knew the non-public information and when. You can cross reference this with data from your trade surveillance system to see if any insiders have made trades in related financial instruments. Your pre-clearance monitoring should prevent them from making such transactions.
4.3 Who does MAR apply to?
The Market Abuse Regulation applies to a range of financial instruments, behaviours and transactions. By definition, any individual or company that trades in these instruments must adhere to the regulation when going about their trading.
5. Conclusion
Understanding the trading activity within your organisation is essential for the sake of compliance and the reputation of your brand. But there are many challenges you must overcome. Using digital systems for pre-clearance and monitoring is instrumental to cutting the work of your compliance department. At the same time, creating a strong compliance culture helps to prevent wrongdoing from occurring.
You can use InsiderLog to create a single source of truth for the personal trades of insiders, with a fast and efficient pre-clearance and PDMR trade reporting process. Request a free demo to see how InsiderLog can work for your organisation.
6. References and further reading
Related Articles
See all postsRegulatory Disclosure: Transparency Directive & MAR Article 17
15-06-25
How and When to Use Permanent Insider Lists (Best Practices)
19-05-25
Managing Insider Lists as an Advisor: 5 Challenges and Solutions
12-05-25
The Ultimate Guide to MiFID II Compliance for Your Team
08-05-25
How to Prevent Financial Misconduct at Your Organisation
24-03-25


.png)
.png)









.png)
.png)













.webp)





